Passkeys: faster, safer, and tricky to get right



Most of the time, convenience and security trade off against each other. Easy access is easier for attackers too. Well, not so with passkeys — this authentication system is super quick to use, super hard to fake, and even harder to leak. The UX upgrade when working with crypto wallets is huge, as you may know from trying Coinbase smart wallets.
Splits' smart wallet system for onchain teams is built around passkeys. As you might guess, we're big fans. Still, this is new tech, so there are potential tripwires that require careful design to circumvent.
Passkeys 101
(Skip this section if you're already well-acquainted.)
Quick primer: A passkey is like a password, but instead of entering a text string, you use… a key. This could be a hardware device such as a YubiKey, or the radically convenient built-in keystore included on your computer or phone, tied to biometric data (fingerprint or face).
Google Chrome documentation succinctly explains:
The difference between passkeys and passwords is that passkeys are cryptographic key pairs. The key pair is specific to a website. One half is shared with the website, and the other half is private and stored on your device or in your password manager. This technology uses a securely generated code to authenticate your access to websites and apps instead of a password that may be stolen or leaked.
Fear not, you don't have to type in that code, or even copy-paste it, because the device does all the work for you. A crucial benefit: "Passkeys are connected to the app or website they were created for, so you can never be tricked into using your passkey to sign in to a fraudulent app or website."
In addition to Chrome browsers, passkey support is built into macOS and iOS as well as Windows and Android. Big Tech, which provides most users' computing platforms, has committed to passkey technology, so it's practical for independent developers of all sizes to get on board. We can safely assume that passkey adoption will increase rapidly and the tooling will continue to improve.
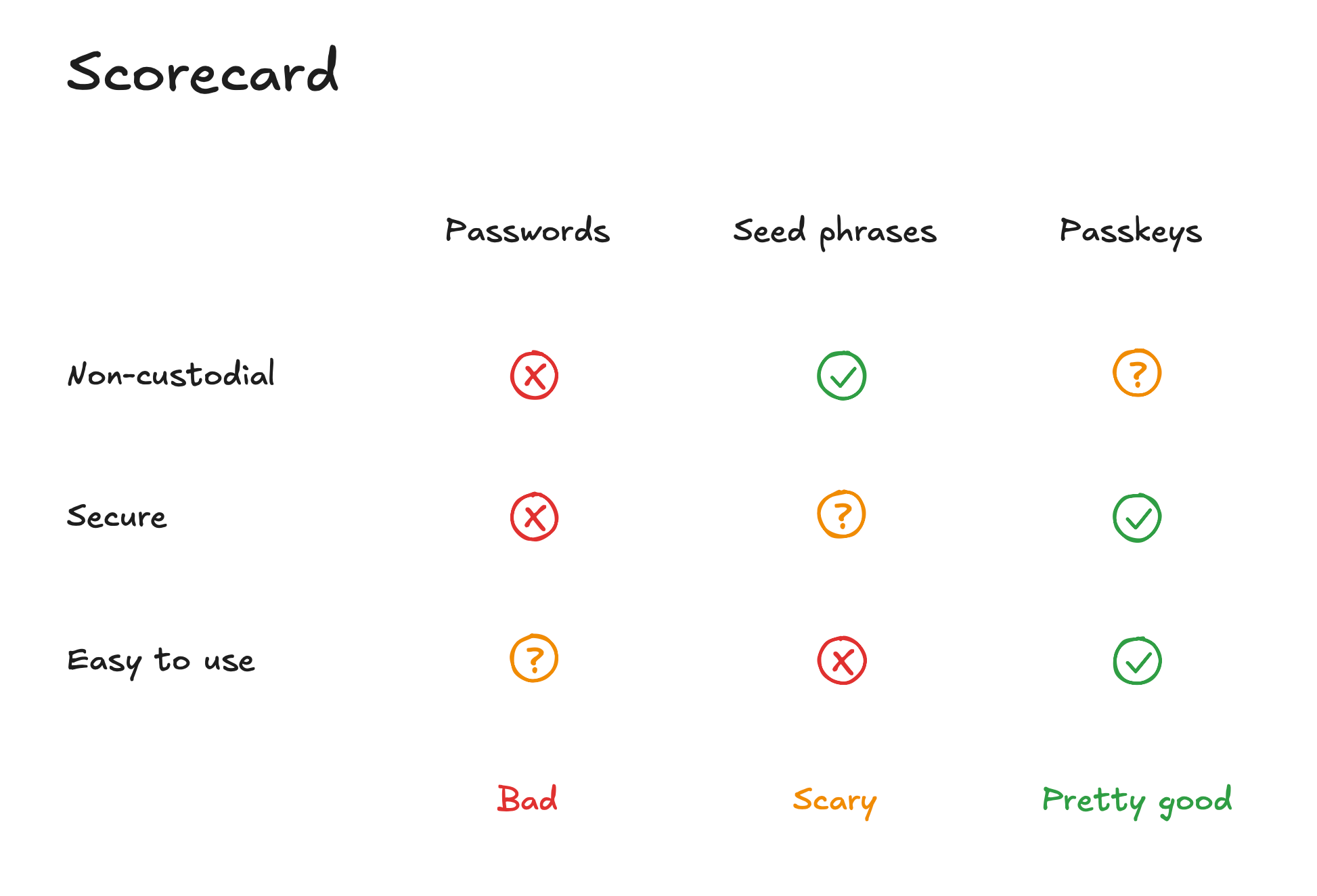
Why passkeys are good
Passkeys are very fast. The user experience is massively better than standard passwords, because passkey integration is native to your browser or operating system. There's no sketchy browser extensions, no need to trust unknown developers — since you already trust Google, Apple, etc., you're not adding a new dependency. And those giant companies have serious account security infrastructure once you dive into the settings.
Even with Big Tech investing in passkeys, you still have the flexibility to choose an external passkey, like a YubiKey, should you prefer to sign with a key that's not on your computer or phone. A YubiKey is even less likely to be compromised, but more likely to be lost, versus your phone or laptop.
Regarding crypto wallets, funds are often lost to human error; luckily native passkeys are coupled to devices that you track closely by default. How often are you out of arm's reach from your phone? While phones and computers can be stolen, there are already robust frameworks for preventing thieves from accessing their contents. (Worth setting up if you haven't already!)
In a crypto context, you can use a mix of passkeys for different types of wallets. For example, your treasury multisig could rely on YubiKeys while your day-to-day accounts could simply use Chrome. A hardware signer has more friction, but not all friction is bad — it can (and should!) be part of your overall security strategy.
For app developers, passkeys are a security boon, in a way that benefits users as well. They are more like magic link authentication than traditional passwords. With passkeys, developers don't store any private key for you on their servers. Developers just store the public key for a user's account, while the private key that actually controls access is stored on the user's own device. That's one less scary pile of sensitive data to guard.
Problems with passkeys
Each passkey is tied to a specific website or service provider, so a given passkey is only as hard as the issuing domain. For example, if you were using a passkey to sign transactions for a wallet and the passkey issuing domain went down, you'd be unable to use it.
Zack Labadie, designer at Magic, raised the issue of "account durability." He pointed out, "Passkeys enable super fast, easy wallet creation but is that really the holy grail? A wallet should serve as a secure, reliable, and accessible identity." At Splits we're confident that this is possible with passkeys… but not passkeys alone. (More on that in the next section.)
A few other problems we’ve discovered that might trip up users and/or developers:
- Not all devices support passkeys, and those that do sometimes have some unique restrictions (Yubikey has a limit of 25 passkeys per device) and behaviors (Chrome overwrites previously created passkeys for the same domain — huh?).
- Some devices/systems try to "hijack" the auth flow — if you have multiple passkeys associated with the same domain (e.g., Chrome, iCloud, 1Password), the passkey providers may clash over which providers gets prompted first (and currently there's little documentation on how to solve this for the user).
- From a development perspective, the reliance on hardware devices can make testing and support more difficult if you want to test on all of them.
- Likewise, working with passkeys across different testing environments is a bit painful (and it's worse the more environments and databases you have).
A temporary downside is that passkeys are still fairly new, so the paradigm is not as well-documented, with fewer guides and instructions for both developers and users. The infrastructure and tools for using passkeys as an app developer still feel primitive (especially interacting with smart contracts). Happily this drawback is lessening as industry adoption accelerates.
A better auth stack
For a long time, all crypto users faced a big tradeoff between usability and security. You could choose between perpetual annoyance or constant nerves. Do passkeys thread that needle? For the most part, we believe they do. Passkeys are not a panacea for all potential security pitfalls, but a big step forward on the whole.
When it comes to wallets, our philosophy is to use passkeys for day-to-day signing, and seed phrases as the escape hatch (think "break glass in emergency"). Splits is a big proponent of using the three account protocol (TAP) and believe TAP combined with passkey- and EOA-based multisig wallets provides the right balance of security and convenience for teams.
Admittedly, you do need more than one passkey per wallet — if your laptop gets stolen or bricked, you can get in with your phone or YubiKey, etc. But once you've created redundant passkeys, the most seamless one (often Chrome) can be your daily driver. The escape hatch — an EOA-controlled multisig — is only necessary when it's really necessary.
In summary, we think the right setup looks something like:
- Follow TAP and separate your assets from your daily wallets.
- Use passkeys-based wallets for day-to-day transactions.
- Use multiple less convenient passkeys (e.g., Yubikey) on a multisig for high-value assets.
- Use an EOA-controlled multisig as an escape hatch.
If this framework interests you, please get in touch on Farcaster — we're looking for feedback on our smart accounts product and would love to hear what you think.
Next, watch Abram's presentation on the passkeys and the auth stack. Or, if you prefer, just browse the slides 😉